Thank goodness for CDs. I don’t know how life is going to change once I can’t own my music.
Look, I know that this whole streaming thing is where you live now. I get it. You’ve got a subscription, and you get to listen to what they provide you, available 24-7 on your phone and computer.
Whatever.
Spotify may be working for you, but it’s not working for me. It doesn’t have what I want to listen to.
Sometimes it does, I guess. But sometimes not. The very first song I tried to find on Spotify this evening was Lene Lovich’s New Toy, a classic on KROQ back in the 80s. And near as I can tell it was on Spotify at one point, at least according to this guy’s playlist that he put together. New Toy is grayed out, for some reason, and doesn’t show up in any searches. I guess it’s gone.
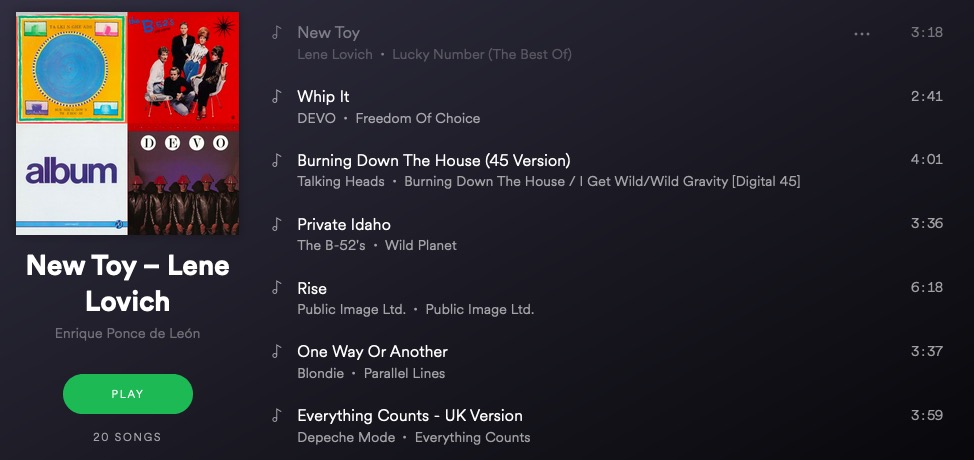
You know what’s not gone? The MP3 on my computer that I legally ripped from a CD that I own.
I had a bit more luck finding Pink Floyd’s Meddle album. Well done, Spotify. And Old Hag You Have Killed Me by the Bothy Band. Excellent. I shouldn’t trash them too much for their selection. They’ve got enough to worry about, what with the criticisms regarding their payment to artists.
Spotify has most of what I want, okay, but it doesn’t have everything I want. The Lene Lovich example above is something you’ve almost certainly lived yourself, perhaps on Netflix when you went to watch a show that you’d seen their before, only to find out that some licensing agreement had expired and the show is no longer available. It happens all the time.
So where music is concerned, I’m still buying CDs. I’ve heard some exaggerated rumors concerning the death of physical media, but it’s not dead yet. I’m buying physical media and ripping it on my Linux box to FLAC (of course), transcoding it to MP3s using the Apple app XLD, and living large.
CDs will go away someday, of course, and I’ll have to get my bits elsewhere. But I dearly hope it’s the bits that I’ll be buying, as opposed to a license to temporary access to those bits, revocable at any time.
In related news, Microsoft has been selling digital books via the Microsoft Store since 2012. Cool, yeah? Oh, wait. Microsoft has pulled Books from the Microsoft Store and is planning to offer customers who’ve purchased any ebooks via the Store refunds, as their books will no longer be accessible as of July, 2019.
Oops. Guess the money I paid for those books wasn’t actually a “purchase.” It was a “user agreement.” My bad.
Hang on to your data, folks. And make backups. ;)